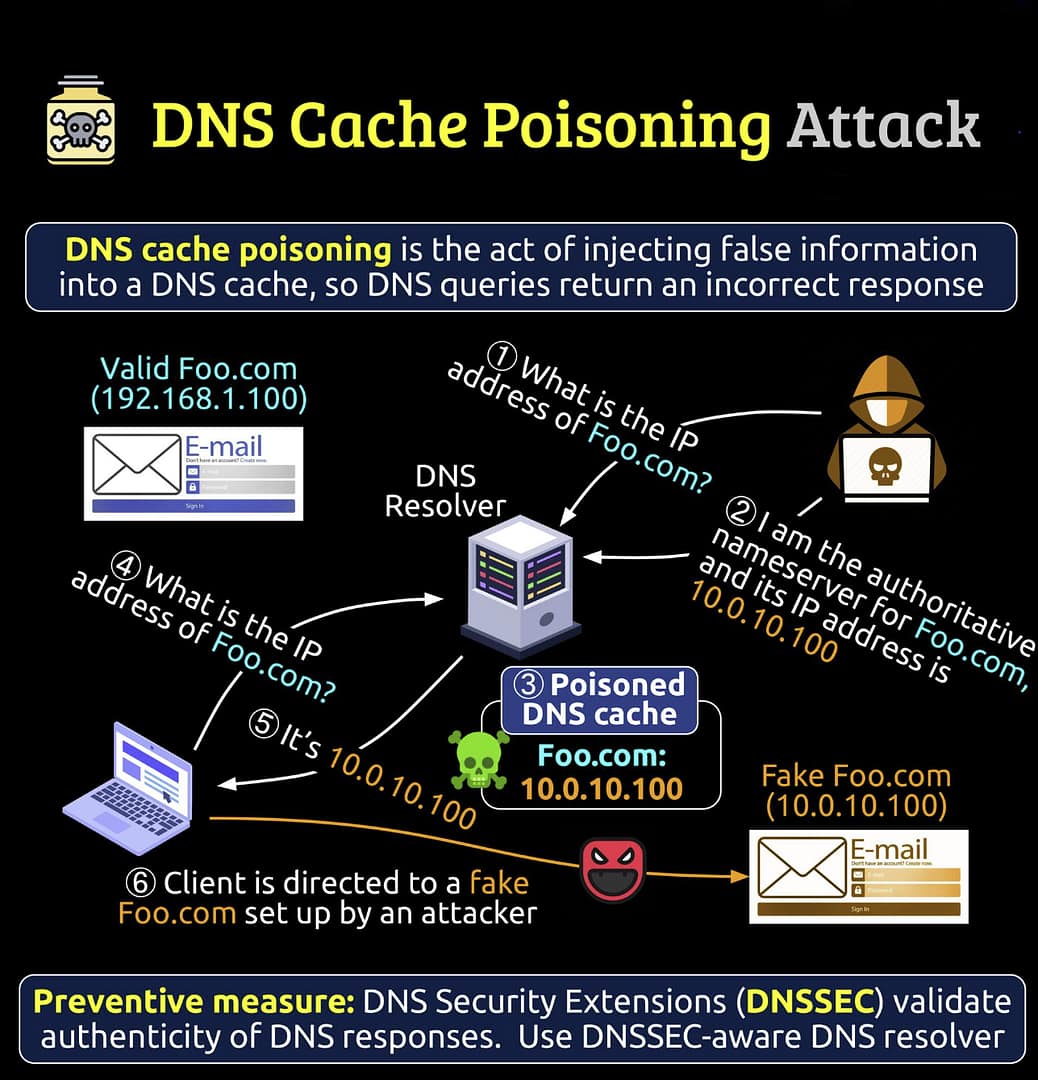
DNS Cache Poisoning, also known as DNS spoofing, is a type of attack where an attacker corrupts the DNS cache of a DNS resolver. By doing this, the attacker can redirect traffic intended for a legitimate domain to a malicious IP address without the user’s knowledge.
How DNS Cache Poisoning Works:
- DNS Query Process:
- When a user attempts to visit a website, their computer sends a DNS query to a DNS resolver (often provided by an ISP) to translate the human-readable domain name into an IP address.
- If the DNS resolver already has the IP address cached, it returns the cached IP without querying the authoritative DNS server.
- Injection of Malicious Data:
- In a DNS cache poisoning attack, the attacker tricks the DNS resolver into caching incorrect IP address mappings by injecting false DNS responses into the cache.
- This is typically done by exploiting vulnerabilities in the DNS software or through man-in-the-middle attacks where the attacker intercepts and modifies DNS queries or responses.
- Impact of Poisoned Cache:
- Once the DNS cache is poisoned, any user querying the compromised DNS resolver for the targeted domain will be directed to the attacker’s chosen IP address.
- This can lead users to phishing sites, malware distribution sites, or other malicious destinations.
- Persistence of the Attack:
- The poisoned cache remains until the TTL (Time-To-Live) of the cached record expires. Until then, all queries for the poisoned domain will return the malicious IP address.
How a CISO Can Protect the Organization:
- DNSSEC Implementation:
- Deploy DNS Security Extensions (DNSSEC) to digitally sign DNS records. DNSSEC ensures the authenticity of the DNS responses by verifying digital signatures, making it difficult for attackers to inject false data into the DNS system.
- Use Secure DNS Resolvers:
- Ensure that the organization’s DNS resolvers are updated, configured securely, and are not using outdated DNS software versions susceptible to known vulnerabilities.
- Use DNS resolvers that support and enforce DNSSEC validation.
- Randomization of DNS Transaction IDs and Source Ports:
- Use DNS resolvers that randomize transaction IDs and source ports for DNS queries. This makes it more challenging for attackers to predict and inject malicious responses.
- Regular DNS Cache Flushing:
- Periodically flush DNS caches to minimize the risk of long-term impact from a cache poisoning attack.
- Monitor DNS Traffic:
- Implement DNS monitoring to detect anomalies or unusual patterns in DNS traffic, which may indicate an ongoing cache poisoning attempt.
- Segment and Isolate DNS Services:
- Use network segmentation to isolate DNS servers from other critical infrastructure. This limits the potential impact of a compromised DNS server.
- Restrict Access to DNS Servers:
- Limit the exposure of internal DNS servers to only necessary internal hosts and services. External DNS requests should be handled by dedicated public-facing DNS servers.
- Employee Awareness and Training:
- Educate employees about the risks of DNS cache poisoning and the importance of reporting suspicious activities, such as unexpected redirects to unfamiliar websites.
By implementing these measures, a CISO can significantly reduce the risk of a DNS cache poisoning attack and ensure the organization’s DNS infrastructure remains secure.